In the intricate dance of digital commerce, where convenience and speed often take center stage, the shadowy specter of fraud lurks in the wings, ever ready to pounce. As businesses and consumers alike wade deeper into the vast ocean of online transactions, the need for robust security measures has never been more pressing. Enter payment tokenization—a formidable guardian in the realm of financial technology, poised to revolutionize the way we protect sensitive information. This cutting-edge solution transforms vulnerable data into unassailable tokens, rendering it useless to cybercriminals and dramatically reducing the risk of fraud. In this article, we will delve into the mechanics of payment tokenization, exploring how this innovative approach not only fortifies digital transactions but also instills confidence in an increasingly interconnected world. Join us as we unravel the complexities of tokenization and uncover its pivotal role in safeguarding the future of digital payments.
Understanding the Mechanics of Payment Tokenization
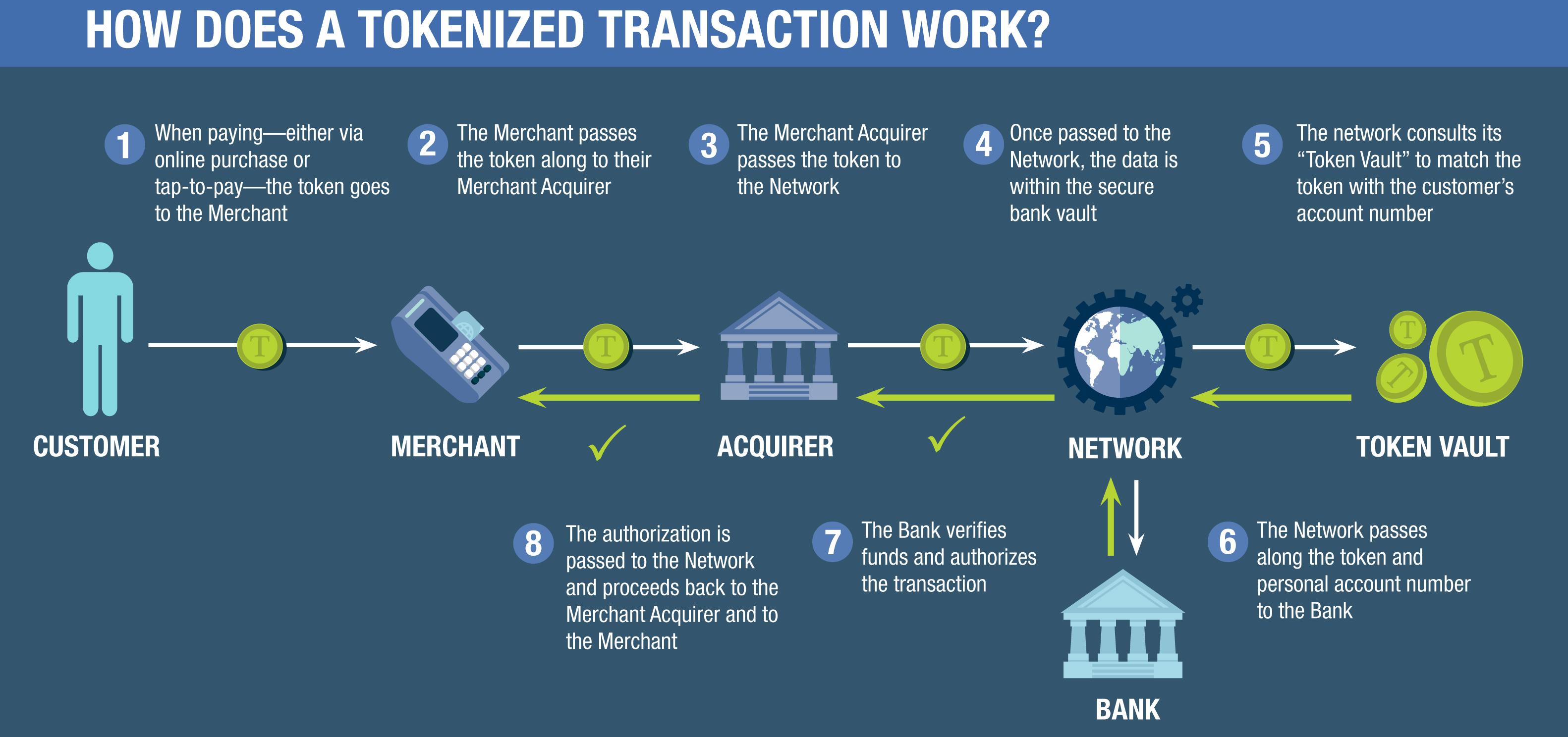
At the heart of modern digital transactions lies a transformative process that significantly enhances security: payment tokenization. This innovative mechanism replaces sensitive payment information, such as credit card numbers, with a unique identifier or “token.” These tokens are meaningless to cybercriminals, effectively reducing the risk of data breaches and fraud. By employing this method, businesses can ensure that the actual card details are never stored on their systems, thus minimizing potential exposure to data theft.
Tokenization offers several key benefits that fortify payment security:
- Enhanced Data Security: By converting sensitive information into tokens, businesses eliminate the storage of actual card data, making it less accessible to hackers.
- Compliance Simplification: Tokenization helps companies meet stringent industry standards like PCI DSS, reducing the complexity and cost of compliance.
- Seamless Integration: The process is designed to integrate smoothly with existing payment systems, ensuring minimal disruption to business operations.
Incorporating tokenization into payment systems not only safeguards customer data but also strengthens consumer trust, paving the way for more secure and reliable digital commerce.

Exploring the Impact of Tokenization on Fraud Prevention
In today’s digital age, where cyber threats are ever-evolving, payment tokenization stands as a formidable shield against fraud. By replacing sensitive payment data with a unique identifier or “token,” this innovative approach ensures that actual card details are never exposed during transactions. This token is meaningless to hackers, rendering stolen data useless and dramatically reducing the risk of fraud. Tokenization, therefore, acts as a powerful deterrent, safeguarding both businesses and consumers from potential breaches.
Consider the advantages of tokenization in the realm of fraud prevention:
- Enhanced Security: Tokens are generated randomly and have no exploitable value, making them a secure alternative to traditional payment methods.
- Reduced Liability: With sensitive data protected, businesses face fewer risks and potential liabilities from data breaches.
- Seamless Integration: Tokenization can be easily integrated into existing payment systems, providing a robust layer of security without disrupting operations.
- Compliance Simplification: By minimizing the storage of sensitive data, tokenization helps businesses comply with stringent data protection regulations more easily.
By leveraging the power of tokenization, companies not only protect their bottom line but also build trust with their customers, creating a safer digital marketplace for all.
Best Practices for Implementing Payment Tokenization
To effectively harness the power of payment tokenization, businesses must adhere to several key strategies. Firstly, it is crucial to partner with a reputable tokenization provider. This ensures that the technology is both robust and compliant with industry standards, safeguarding sensitive data from potential breaches. Additionally, integrating tokenization seamlessly with existing payment systems is vital. This not only enhances security but also maintains a smooth user experience, preventing any disruptions in the payment process.
Furthermore, ongoing monitoring and regular audits of the tokenization system are essential to identify and address vulnerabilities promptly. Training employees on the importance and functioning of tokenization can further fortify security measures, as informed staff are better equipped to handle potential threats. Finally, keeping abreast of the latest developments in payment security technology ensures that your tokenization practices remain cutting-edge and effective in mitigating fraud risks.
Leveraging Tokenization for Enhanced Security in Transactions
In today’s digital age, safeguarding sensitive financial information is paramount. Payment tokenization emerges as a formidable ally in this quest, transforming traditional security paradigms. By substituting sensitive card details with a unique identifier or “token,” this technology significantly reduces the exposure of actual data during transactions. This token, which is essentially a randomized string of characters, is useless if intercepted, as it cannot be reverse-engineered to retrieve the original information. Tokenization not only fortifies the security framework but also ensures that merchants and service providers handle less sensitive data, minimizing their liability and compliance burdens.
Key benefits of payment tokenization include:
- Enhanced Data Security: Tokens are generated uniquely for each transaction, ensuring that sensitive information is never stored or transmitted.
- Reduced Fraud Risk: Since tokens are worthless outside the specific transaction, they significantly mitigate the risk of data breaches and fraud.
- Compliance Simplification: By limiting the handling of sensitive data, businesses can streamline their compliance with regulations like PCI DSS.
- Improved Customer Trust: Customers are more likely to engage with businesses that prioritize their data security, fostering long-term loyalty.
As businesses continue to navigate the complexities of digital transactions, adopting tokenization is not just a strategic advantage but a necessity in maintaining robust security standards.





